top of page
Search

Case Study : UAV Security Management
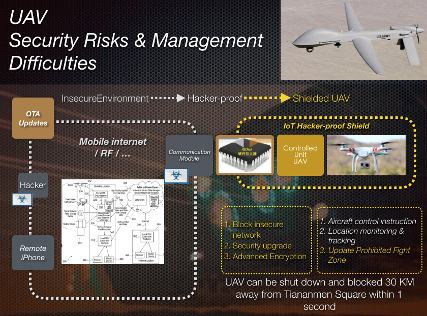
If a UAV communication module is compromised, the drone could be remotely hijacked and misused for criminal activities. However, by integrating an iSDNA hardware firewall between the flight module and the communication module, we can ensure that only authenticated devices—such as authorized smartphones and backend control systems—can issue commands.
Steven Chang
Dec 28, 20203 min read
bottom of page