iSDNA Advantage : Better then eSE / ARM TrustZone ..
- Steven Chang
- Dec 28, 2020
- 3 min read
Updated: Mar 27, 2025

iSDNA Advantage
The current security protection mechanisms for IoT and the entire internet follow a common structure. Both the cloud and client layers primarily rely on passive protection, similar to eSE and ARM TrustZone.
This process can take over a year, as it involves multiple phases—from detecting hackers and security incidents to identifying vulnerabilities and developing patches.
Only iSDNA's cloud protection mechanism can proactively safeguard IoT-controlled devices against unknown vulnerabilities and cyberattacks.
Below is an analysis of security strategies in the industry.
The following is a discussion on the security plan of the industry.

Comparison: iSDNA vs. Other Security Solutions
1. Superior Security
iSDNA provides stronger protection for IoT communication modules compared to TrustZone and eSE because hackers cannot bypass iSDNA authentication.
2. Instant Deployment
iSDNA offers seamless industry integration with no modifications needed to existing industry designs. Simply install our chip between the communication module and the control unit.
iSDNA manages security protocols and encryption, making encryption key management more efficient.
In contrast, TrustZone faces multiple challenges:
Requires changing the communication controller to an ARM architecture.
Involves complex industry integration, encryption key management, and an asset key exchange platform.
Has a longer value chain, increasing dependency on industry-wide cooperation.
Our solution is simpler, more adaptable, and complies with various national security policies.
3. Cost-Effective
eSE-based security architectures incur higher costs due to IoT communication module maintenance, updates, and diverse circuit designs for different chip specifications.
TrustZone for NB-IoT requires Linux AP support and a SIM authentication mechanism, leading to large application sizes (often exceeding megabytes) and significantly increasing deployment complexity and cost.
iSDNA, in contrast:
Supports multiple security standards via a lightweight Java Applet.
Allows SIM authentication applet installation in NB-IoT environments to reduce costs.
Requires only a few kilobytes per module for security and business updates, cutting operational expenses by hundreds of times compared to TrustZone and eSE solutions.
Current IoT Security Challenges (eSE-based Architectures)

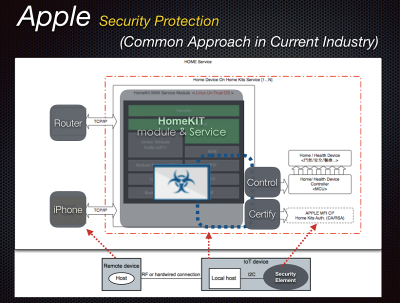
The most common IoT security architecture today is eSE-based, which is widely used in the industry. For example, Apple HomeKit follows a similar security model.
Example: Apple HomeKit
HomeKit integrates Wi-Fi into IoT communication modules and uses HAP/WAC service frameworks.
Apple employs PKI authentication in the certification processor to verify iPhones and facilitate secure communication between HomeKit devices over Wi-Fi.
However, this structure is vulnerable:
In 2023, MediaTek discovered a remote Wi-Fi vulnerability that allowed attackers to gain root access.
Once root access is obtained, security authentication is bypassed, making all protections useless.
This remains a major unsolved issue in the industry—communication module security is not adequately addressed.
iSDNA vs. ARM TrustZone

ARM TrustZone: Limitations & Risks
ARM TrustZone divides the system into:
Rich OS (Insecure)
Trust OS (Secure)
It relies on a monitoring mechanism to manage instructions, interrupts, and memory register exchanges. However, this approach has significant security flaws:
Since memory register management is centralized, memory overflow attacks are easily executed.
TrustZone's monitoring mechanism operates within the Linux kernel, making it vulnerable in open-source environments.
Governments and hackers could potentially manipulate the system or introduce hidden backdoors, particularly in markets like Chinese smartphone manufacturing.
Even with EAL6+ certified hardware, TrustZone does not guarantee security.
Industry-Wide Security & Business Model Issues
Qualcomm has proposed a $1 EAL6+ NB-IoT module, but security concerns persist due to open-source vulnerabilities.
iSDNA has achieved higher security levels:
Hardware: EAL6+ certified
Software Kernel: EAL4+ (targeting EAL6+ certification in the future)
ARM TrustZone cannot achieve EAL6+ certification due to its reliance on an open-source OS, which remains susceptible to root access exploits.
In 2023 alone, three critical security threats were discovered in ARM TrustZone.
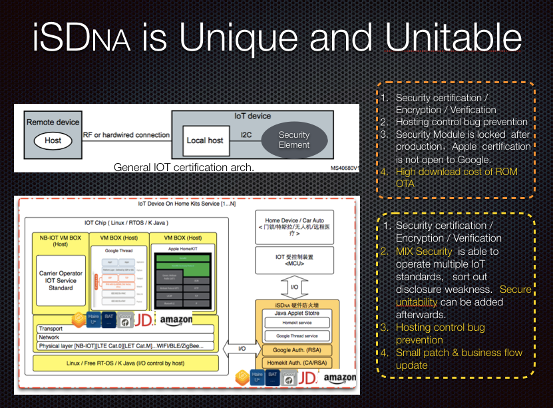
Industry-Wide IoT Certification Challenges
Current IoT certification frameworks suffer from several major weaknesses:
Limited security mechanisms inherited from pre-installed device architectures.
Inability to defend against future bug threats and attacks.
Lack of cross-brand compatibility for security standards.
High maintenance costs for security updates.
The iSDNA Advantage
iSDNA offers a unique security solution that overcomes these industry challenges:
Security-as-a-Service – Enables continuous security updates for deployed devices.
Proactive Bug Isolation & Instant Alerts – Detects and mitigates new vulnerabilities before they can be exploited.
Cross-Brand Compatibility – Supports multiple applications and dynamic updates for secure cross-brand collaboration.
Reduced Maintenance Costs – Allows flexible product updates while minimizing post-sale service expenses.
Cuts IoT operational costs by 100x compared to current architectures.



Comments